Coronavirus emergency is being used to spreads dangerous Emotet trojan.
We have seen cybercriminals exploiting global events such as theFootball World Cup, Christmas or disasters like missing Malaysia Plane (MH-370) to spread malware or misguide masses. But, this time, Coronavirus, a global health emergency is being used by crooks to not only spread malware butsiphon off sensitive and personal data from unsuspected users.
Cybersecurity firms IBM X-Force and Kaspersky have identified a new campaign in which botnet-driven, malware-infected emails are being sent to unsuspected users. What makes it utterly disgusting is the fact that scammers are using coronavirus theme to trick the recipient into opening it.
Reportedly, these emails contain attachments, which are promoted as notices containing details of coronavirus infection prevention measures.
It is indeed ironic that scammers are using the name of coronavirus to distribute another malware widely known as the Emotet Trojan. Previously, the Emotet malware was distributed through corporate-style payment invoices and notification emails only, but this time around the impact of the campaign will surely be higher given the global nature of coronavirus infection scare.
IBM X-Force observed that a majority of these emails are written in the Japanese language, which suggests that the attackers are deliberately targeting users from locations most affected by coronavirus outbreak.
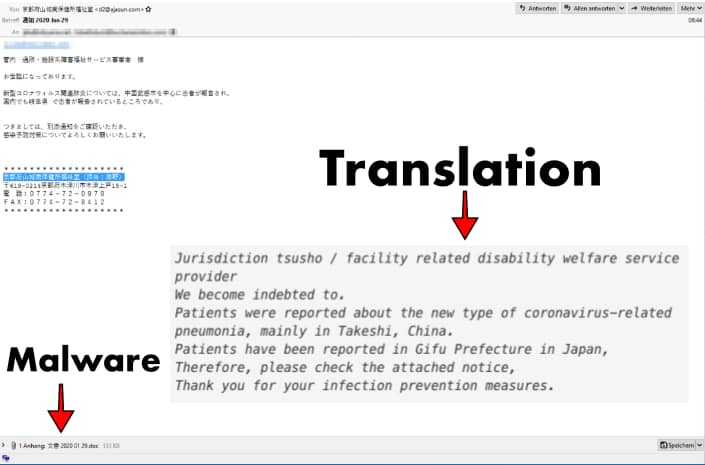
The subject line of the emails contains a Japanese language word that means notification, and displays the current date to generate an environment of urgency. Furthermore, the emails are disguised as infection prevention information sent by a Japan-based disability welfare service provider.
Here’s what the email looks like:
In a blog post, IBM X-Force team wrote that:
“The text briefly states that there have been reports of coronavirus patients in the Gifu prefecture in Japan and urges the reader to view the attached document.”
There are several versions of the email, all having the same language but highly different Japanese prefectures such as in some it is Osaka while in some Tottori is mentioned. The email ends with a footer displaying an authentic mailing address, fax and phone number of the targeted prefectures’ relevant health authority.
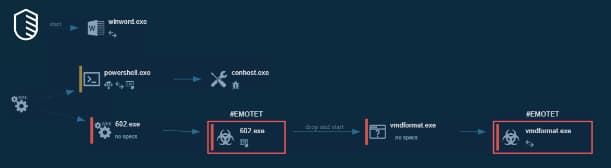
Apart from using the coronavirus theme, the rest of the campaign strategy is rather mundane. When the recipient opens the attached document, an MS Office 365message appears asking the user to enable content in case the document opens in a protected view.
If the document opens with macros enabled, a hidden VBA macro script enables PowerShell to activate the Emotet executable and download the malware. It is the same technique used in all the previous Emotet email campaigns, said IBM X-Force researchers.
However, Kaspersky states that the Emotet malware campaign is just one of the many campaigns utilizing the coronavirus scare to attract unsuspecting users. They have identified 10 different documents aiming to infect devices using coronavirus theme.
“The discovered malicious files were masked under the guise of .PDF, .MP4, .DOC files about the coronavirus [containing] video instructions on how to protect yourself from the virus, updates on the threat and even virus-detection procedures.” But, actually delivering Trojans and worms that can destroy, block, copy or modify data or interrupt computer/network operations, explained Kaspersky researchers.
Coronavirus originated in China’s Wuhan province and rapidlytransformed into a global health crisis. Apparently, scammers and cybercrooks have nothing to do with the planet as they consider it a wonderful opportunity to infect a few devices. Users must not click on such emails or download attachments to protect their device.