NOKIA 7 PLUS PHONES SENT PERSONAL INFORMATION TO China.Nokia 7 plus phones have been hidden sending personal information to China. Finland has started an investigation after NRK’s disclosure. As per NRK’s reports, The end user’s phone number, GPS location, mobile phone IMEI number has sent to the Chinese server. Every time when Nokia 7 plus devices were powered on or Unlocked the information sent to the server. Moreover, the data packages were in an unencrypted format that is more horrify. NRK investigated and found the server domain vnet.cn. Vnet.cn domain is own by China Internet Network Information Center( China Telecom). Likely, that this is an application intended for the Chinese market but which has been accidentally distributed to Nokia 7 Plus phones outside China’s borders. HMD Global refused to make comment to NRK on the matter. Further more, uncovered code on Github by non-other than Qualcomm. The only other clue comes courtesy of security researcher Dirk Wetter, wh
Posts
Showing posts from March, 2019
All people in East Africa who use mobile phones are at a risk of falling prey to cyber criminals
- Get link
- Other Apps

C Throughout my writings and research reports i have presented to various blogs, websites,and as an experienced cyber security and threat intelligence analyst.I have for long time been warning all of you in East Africa of being subjective and prone to attacks from cyber criminals.I remember telling you of the behavior that show a phone or an technology equipment has been taken over by a malicious spy ware or any exterior intrusion. Some of the characters include fast draining of the battery,unfamiliar sounds in background when calling,slowness and unexpected shutdowns of internet browser and search engines.... etc. Recently you had that president Uhuru Kenyatta's social media accounts were being intruded by unknown and anauthorised people!!!! How did it happen for a whole president with all availed technocrats. Its ridiculous however we as technologists know that it is possible. I have talked of many issues which President Uhuru Kenyatta's technocrats can put in
- Get link
- Other Apps

I have been investigating this online fraud by the one who claims is a brian white foundation ti help people...... Thisbis fraud,deal with him at your own peril Him and otherbmanyfraudulent people who think can use social.Media to con people should stop There are other characters who want to blackmail the gorvenment,important personalities should also stop... We all have the right to expression but we shouldbuse it not to harm others
SU-57 is the deadliest multirole air fighter
- Get link
- Other Apps
The Swedish jet has no outstanding characteristics in comparison to the fifth-generation Su-57’s, but reportedly has top of the line electronic warfare (EW) equipment and software, making it difficult for enemy jets to track it. Commander of Sweden's Air Force, Mats Helgesson, stated that the country's recently developed Saab JAS 39 Gripen E jets were "designed to kill Sukhois" — Russia's top air superiority fighters, Finnish national broadcaster Yle reported. In a bid to further stress the Gripen E's effectiveness, Helgesson concluded that the aircraft have a "black belt" in fighting Russian jets. Justin Bronk, an aerial-combat expert at the Royal United Services Institute, cited by Business Insider, said that the JAS 39 Gripen series is known for its outstanding EW capabilities, which are upgraded every two years. "Several years ago the Gripen pilots got tired of being made fun of by German Typhoon pilots and came to play with their warti
Who has been intruding in president Kenyatta's social media accounts
- Get link
- Other Apps
Like i have been alerting you for long,our socail media accounts are not secure!!! I have always told you that 2FA (two factor authentication) cannot help you.i proved this on gmail,yahoo,facebook,instagram..The process of sending us security codes as proof of our security is just bogus. Alot of social media accounts here in africa are prone to ss7 exploits and other state sponsored intruders.i remember telling via my facebook account around mid this month how a certain country had managed to sneak into accounts of its citzens whom it thought were ill talking about its situation.i had proved that after a mishap in Facebook's usual way of working. On gmail,there are certaim spam messages telling you of bank accounts loaded with money or scholarships where you are convinced to tap on the links with faces of beautiful ladies.This is a dangerous link do not dare try it. Sometimes when you are logged into your account,you see changes in the font size of your page yet you did not invo
How to set up two step verification on your social media account
- Get link
- Other Apps
One of the most remarkable developments in the consumer technology industry in the past two decades is the emergence of social media networks. Social media has revolutionized the sort of social connections and interactions we have offline. Additionally, it has enhanced how we communicate and stay informed. Nowadays, billions of people around the world use one or several of the existing social networking platforms daily to communicate with family, friends, and colleagues. Also, many of us use some of our social media accounts to stay abreast with events and current affairs happening around us and in the lives of those we are connected with on the networks. Although it has its demerits, social media has indubitably brought great benefits to us. With all the attractions of social networks, it’s easy to get immersed in your online engagement and forget an essential aspect of your digital life — security. However, the risk of account breach (unauthorized access) by bad actors with n
Turkey blames Saturday bombs by the alshabab in somalia
- Get link
- Other Apps
Close to 20 people among them a deputy minister were killed in multiple bombing attacks in Mogadishu and its environs. Al-Shabaab militants drove into the Ministry of Labour office block leaving in its wake at least ten dead and ten others injured. Deputy Labour Minister Saqar Ibrahim Abdalla was among those killed in the 11 am bombing. According to some tabloids,police sources said that about ten bodies had been retrieved from the building which also houses the ministry of public works in Shangani area. Ambulance service Aaamin Ambulance said it had ferried ten injured people to various city hospitals. The entrance to the Ministry of Labour building damaged when an explosives laded vehicle rammed into it. An explosives loaded vehicle rammed into the building followed by heavy gunfire as security forces engaged the militants in gunfire. Three explosions went off within a span of 15 minutes. Police said all the militants had been killed. three other bombings hit various p
Android Q developer beta may be launched today
- Get link
- Other Apps
Android Q , the next version of the mobile operating system, could be launching its developer preview later today, thanks to speculation over a date filter in Google’s bug tracker. A template explaining how to file bug reports for Android Q Beta was spotted by XDA Developers Editor-in-Chief Mishaal Rahman. The sample (which reportedly could be found here but has since been removed) seemed to be directed at OEMs, and advises reporters to check if the issue has already been filed by clicking a link ( https://goo.gl/qL5TjA , still working as of publication) leading to a repository – which only lists bug tickets created on or after March 11, 2019. Apple invites went out for its March 25 event, where it might announce a streaming service Samsung: use the fingerprint scanner , not facial unlocking, for more security "I took selfies with the Huawei Mate X foldable and it's a game-changer" Expanding beta This comes hot on the heels of another revelation that Google will
- Get link
- Other Apps

Researchers at Kaspersky Lab have uncovered a new strain of malware spreading via The Pirate Bay torrent tracker site. Named after the classic Russian doll , PirateMatryoshka aims to infect users ’ computers with adware and tools that spreads further malware onto the device . It carries a Trojan -downloader disguised as a hacked version of legitimate software used in everyday PC activity. Torrent services are a popular target for cybercriminals looking to distribute malicious code, not least because users in search of illegal content often disconnect their online security solutions or ignore system notifications in order to install the downloaded content . PirateMatryoshka is spread using established seeders with no known history of malicious activity. The latter makes for an effective distribution process , because due to the good reputation of the seeder , potential victims have no reason to doubt that the file to be downloaded is safe . Once the installer is run it shows t
- Get link
- Other Apps
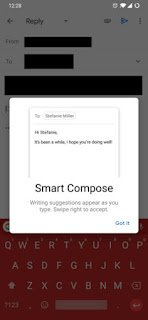
The Gmail Smart Compose feature is a nifty time-saving service that uses AI and machine learning to suggest words and sentences while you compose emails. Those that use it find it to be fairly accurate and legitimately helpful. However, those that have been using it have been Google Pixel 3 owners, as Smart Compose has only been available on that device. Not anymore, though! Starting now, Smart Compose is rolling out to everyone, regardless of your smartphone’s make or model. Simply fire up the Gmail app and, assuming you’re on the latest version, you should see the following pop-up: For reference, that appeared on my phone Now, when you are typing an email, you should see suggestions here and there that will help you autocomplete your sentence If for some reason you don’t want this feature, that’s OK: Google allows you to turn Smart Compose off. Just open Gmail, open the flyout menu, scroll down to Settings, choose the appropriate account, and then uncheck “Smart Compose.” Re
TWRP for Samsung s9 and s9+ is now officially available
- Get link
- Other Apps

Many of Samsung's phones, including its flagship Galaxy S and Note series, ship with different processors depending on where they are sold. Some models have the company's own Exynos chips, while others have Snapdragon processors. Almost one year after the phone's release , the TWRP custom recovery now has official builds for the Snapdragon Galaxy S9/S9+. The recovery image is specifically for the SM-G9600 (S9) and SM-G9650 (S9+) models, which are sold in Hong Kong and Latin America. Those of you with a United States S9 are still out of luck, since Samsung doesn't allow bootloaders on those phones to be unlocked. Recovery images for the Galaxy S9 ( starqltechn ) and S9+ ( star2qltechn ) are available from TWRP's website
- Get link
- Other Apps
Kagame’s insanity: Rwanda asks Museveni to kick out top tycoon. By: sadabkk@observer.ug There are many reasons argued publicly and privately by officials on both sides of the conflict for the current border standoff between Rwanda and Uganda, but government insiders have nailed it down to one: Kampala’s outright refusal to turn against a very prominent Rwandan businessman hugely invested in this country. Two weeks before Rwanda closed its borders with Uganda on Wednesday last week, the Rwandan high commissioner to Kampala met President Museveni and communicated several requests for action against particular dissidents. A well-placed government of Uganda source has told The Observer that Maj Gen Frank Mugambage reportedly arrived with, among others, a request that Uganda should close businesses owned by Tribert Rujugiro Ayabatwa, a very wealthy Rwandan national running a string of enterprises in Uganda. The Rwandan government believes Rujugiro is pumping money into subversive activ
Arrested for selling a gun
- Get link
- Other Apps
The Chieftaincy of Military Intelligence is holding an armour man at Kampala Central Police station for selling police guns. Sgt Hannington Mugungira is being detained at CMI manned Special Investigations Division in Kireka after police guns went missing in February this year. It is reported that during the audit, guns we discovered missing and further probe discovered that Mugungira had sold two pistols. A source at Kampala CPS told one tabloid, that the suspect admitted that he sold the pistols which further led CMI operatives to the arrest of a one Akampulira from Maestro Security Company who is the buyer of the said guns. Luke Owoyesigire the Kampala Metropolitan deputy police spokesperson when contacted for a comment said the matter was being handled by CID headquarters in Kibuli. Owoyesigire referred this online newspaper to SP Vicente Sekate the CID spokesperson for more details but could not be reached by the time of press. Six Police officers were in 2017 arrested at Ka
Are you safe with your huawei phone?
- Get link
- Other Apps
Cyber-espionage has been going on for years. In one famous example in 2012, it emerged that China had hacked UK defense firm BAE Systems to steal data about a $264 billion F-35 Joint Strike Fighter (JSF) jet. And it wasn’t the first time the country had been accused of stealing military jet plans. But recently, the focus has moved to Chinese companies, particularly those that manufacture network equipment as 5G services start to roll out. So, why is all the focus on Huawei, and how secure is it to use its products and services? Founded in Shenzhen, Guangdong, in 1987 by Ren Zhengfei, a former People's Liberation Army officer, the firm is owned by 80,000 of its 180,000 employees. Like its rivals Nokia and Ericsson, Huawei has manufactured mobile network equipment for years. During the last decade or so it has stormed into the consumer market as a smartphone manufacturer and now owns 16% of the market. At Mobile World Congress (MWC) this week, it became the latest to announce a f
F35 is a turd with wings...?
- Get link
- Other Apps

the F35 is a turd with wings...? Its not like the General Accounting Office (GAO) created a report citing "111 Category 1 and 855 Category 2 deficiencies". . . Its not like it will 'fall out of the sky' if it is disconnected from Autonomic Logistics Information System (ALIS) for a short amount of time. . . It is not like the F35B variant 'shook apart under stress-testing' and has to have its tyres changed in less than 10 landings. . . Its not like the guns on the F35 are "consistently missing ground targets" and are showing a bias “long, and to the right”. . . The Lockheed Martin F-35 Joint Strike Fighter was supposed to be four times more effective than older, legacy fighters in air-to-air combat, Eight times more effective in air-to-ground combat, And three times better at reconnaissance and suppression of enemy air defences. All 3 versions of the F35 (A, B & C) are zesty yellow turds. Not only has the project extremely over promised an
Bitcoin developer ,jameson lopp explanations on how to be secure on Bitcoin
- Get link
- Other Apps
More people are thinking about online privacy and protecting their data these days, but how hard is it to close every potential data leak and keep your personal information secure? On a recent episode of Epicenter , Casa CTO Jameson Lopp explained the extreme measures he takes to protect his privacy in an increasingly digital world. ‘They Don’t Know My Real Name’ After discussing why online privacy is so important in the age of social media, Lopp was asked to explain the tradeoffs of trying to close up all of the potential security holes in his daily life in the aftermath of a swatting incident in 2017 . Lopp gave examples of some of the extreme measures he has taken, including the use of a fake name when interacting with the people who live near him. “They don’t know my real name,” said Lopp. “They don’t know what I do. They just know that I’m a programmer. I’m a boring old programmer.” Lopp added that he interacts with most of his friends remotely via the internet, and he doesn’
Facebook has again been lying its users!
- Get link
- Other Apps
Facebook's 2019 looks set to repeat the PR train wreck of 2018, with the company now admitting that they misrepresented the extent of their spying on teenage user data when the controversy came to light in January this year. Significantly more kids were affected than originally acknowledged and parental consent was nothing of the sort. This comes a day after Instagram was slammed for being the worst social media culprit for facilitating child abuse. Any relief the social media giant may have been feeling following January’s record results, and consigning 2018 to the history books, now seems to be fading away. At the end of January, the news broke that Facebook has been secretly paying people to install a 'Facebook Research' VPN to harvest users' phone and web activity. The program deployed a VPN that bypassed the app store safeguards, granting access to private messages and chats, web activity and emails open. Last year, Apple removed the Israeli Onavo app , acqui
- Get link
- Other Apps

When eBay merchant Mr. Balaj was looking through a pile of hi-fi junk at an auction in the U.K., he came across an odd-looking device. Easily mistaken for a child’s tablet, it had the word “Cellebrite” written on it. To Mr. Balaj, it appeared to be a worthless piece of electronic flotsam, so he left it in his garage to gather dust for eight months. But recently he’s learned just what he had his hands on: a valuable, Israeli-made piece of technology called the Cellebrite UFED. It’s used by police around the world to break open iPhones, Androids and other modern mobiles to extract data. The U.S. federal government, from the FBI to Immigration and Customs Enforcement, has been handing millions to Cellebrite to break into Apple and Google smartphones. Mr. Balaj ( Forbes agreed not to publish his first name at his request) and others on eBay are now acquiring and trading Cellebrite systems for between $100 and $1,000 a unit. Comparable, brand-new Cellebrite tools start at $6,000. Ce
- Get link
- Other Apps

el some of you should start being careful of what comes out of your beaks!!!! i know that such people who post such want gain attention ....and later on start deceiving that CMI,ISO,CID,SFC operatives are hunting you because of what your dirty minds compels you to write.Let warn you,its high time you start avoiding jokes about Security!!!!! now ,what if they ask you when,how and where in kisoro you saw those army vehicles, what would you say???? By the way,some of you are not ever worth to be thought of by CMI and i think some of you have never seen real CMI or ISO,SFC....you really have not!!!!
- Get link
- Other Apps
Cellebrite UFED, an iPhone hacking tool made in Israel and widely used by the law enforcement authorities including the Federal Bureau of Investigation, Customs Enforcement and Immigration departments is surprisingly up for sale on eBay. This tool is mainly used for hacking or breaking open modern mobile phones such as iPhones and Androids for the sole purpose of obtaining data. The law enforcement authorities primarily use Cellebrite to extract data from Google smartphones and Apple devices . It is the same iPhone hacking tool that the FBI used to break open the iPhone 5C of Syed Rizwan Farook , the infamous San Bernardino shooter. See: Textalyzer Device Tells Police Everything Users Do on Their Smartphone According to Forbes , second hand Cellebrite is being sold on eBay between $100 to $1000. It is worth noting that Cellebrite sells new tools for $6,000. Understandably, Cellebrite, a forensic data firm responsible for making Cellebrite UFED, isn’t happy about it and has warned c