Facebook,Instagram and Google users are again at a risk of intrusion,.I have warned facebook.com and MTN Uganda over this security hole.. iqm Wondering how a local phone number sends a security verification code before Facebook sends it... I have been testing the security of my social media accounts and today I was shocked,a local phone number sent me a security verification code first and then Facebook sent the same code later!!! And I real know that this is very abnormal.... I have been alerting all telephone communication companies in East Africa about this insecurity!!! Citzens using phone numbers and email accounts are at a danger of loosing their data!!!! Something should be done to iron out this nonsense.....
An experienced CYBER SECURITY ANALYST dealing in transborder crimes on phones,computers,threat intelligence, bug hunting,.... White hat hacking and Repairing phones and reviewer of new technology gadgets
Monday, April 29, 2019
Tommorow 01/05/2019 all phone numbers not verified and confirmed against NIN will be switched off!!!
As MTN Uganda tries to iron out all the shortcomings in the database of the registered phone numbers,it set tomorrow as the day all phone numbers not confirmed against the national Identity cards will be put off air!!! I applaud MTN Uganda for this,alot of issues have been unexplainable due to some of these dubiously registered numbers
Am now presenting you a way you can verify and confirm phone numbers registered on ,of and against your national ID
HERE WE GO
The code for confirming your registration is *197# and when you dial, it’ll give you the options below: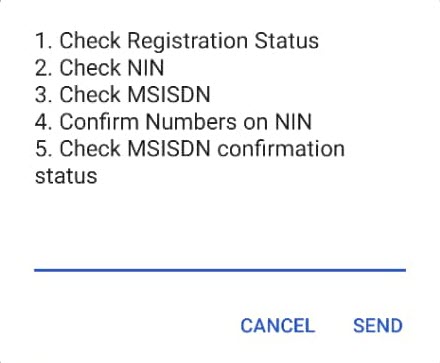

When you pick option 1, you’ll be able to know whether your number is registered.
But when you pick option 4, the following will appear.
It should be noted that by selecting option 1 (from above), you’ll verify MTN number(s) that are registered against your NIN.
When you select Option 2, you’ll remove numbers registered against your NIN one by one.
When you choose option 3, you’ll be able to add back numbers you might have removed accidentally.
If your identification details are not captured, visit any MTN Service Centre or Dduuka to verify all numbers registered against your NIN.
The numbers you remove from your NIN will be barred immediately and KYC details deleted. And those that you allow will take on the name on the National ID.
To see all numbers registered against your NIN, you’ll dial *197#, select option 2 and enter your NIN.
Citzens have done a great work in the arrest of an armed robber
Vigilant residents arrest armed man
Residents of Kiwatule this afternoon foiled an attempted robbery in Kiwatule after gunman entered Liquid Cash Emergency Loans with intent to rob.
The suspect, Isaac Mulengenyi, 23, reportedly fired in the air to scare onlookers however mob charged at him, arrested and handed him to police.
A case of aggravated robbery has been opened at Ntinda Police Station Vide CRB 123/2019 while a rifle has been recovered with nine rounds of ammunition.
The suspect is still being detained at Ntinda pending appearance before court.
Somalia and the alshabab today!!!!
Security forces in Mogadishu have last night conducted a massive operation aimed to sweep suspected Al-Shabaab militants groups in the city.
The night operation which was conducted in Dharkenlay district of Banadir region led to the arrest hundreds of young people.
Police said the hundreds of the young people who were taken to custody will be questioned with a view to getting more information from them.
The governor of Benadir region and mayor of Mogadishu, Abdirahman Osman Yarisow has yesterday vowed to ensure the safety and security of the capital Mogadishu.
Security forces in Banadir region have been conducting security operations in Mogadishu over the past few months to ensure the security of the region.
Again on this sunday ,Kenyan police urged the public to provide any information that will lead to the arrest of three wanted terror suspects behind insecurity across the East African nation.
Anthony Munga, National Police Service’s deputy spokesman also circulated photos of the suspects whom he said could be armed and dangerous and may cause harm to the public and urged the three suspects to surrender themselves.
“We urge those who suspect that their relatives or acquaintances could have joined jihadi groups, are planning to travel to jihadi theatres, or have returned from countries known to harbour jihadists to immediately report to the nearest police station,” Munga said in a statement issued in Nairobi.
Munga who did not provide names of the wanted terror suspects said the police have already started taking legal action on individuals who have failed to report on their associates and relatives who have joined jihadi organizations.
Kenya is currently engaged in the fight against the militia group in southern Somalia where its soldiers under the African Union peacekeeping mission African Union Mission in Somalia (AMISOM) have intensified the fight against the insurgents.
The east African nation faces insecurity as bomb attacks using improvised explosive devices and grenades have targeted the coastal city of Mombasa and northeastern regions since the military entered Somalia in 2011 to secure the shared border Somalia. court in Mogadishu has today,Monday sentenced to death a police officer found guilty of killing a minibus driver and injury one of the passenger on 06-01-2019 at Siinka dheer a police checkpoint between Mogadishu and Afgoye
Colonel Hussein Mohamed Mohamud, one of the judges of the Supreme Court of the Armed Forces read the verdict to the media and declared that Abdullahi Hassan Mohamed Ali has committed the crime deliberately and killed Mohamed Ismail Qaboobe on 6th January this year at Siinka dheer.
“Abdullahi Hassan Mohamed has also injured unarmed civilians who were on board of the minibus driven by the deceased Mohamed Ismail,” added Colonel Hussein.
The judge noted the defendant can appeal the case.
The military court often carries out sentences and executions to Al-Shabaab militants and government soldiers who commit crimes despite condemnation from human rights groups including the European Union.
The African Union Mission in Somalia (AMISOM) on Saturday dismissed reports that extremist group of al-Shabab has recaptured the recently liberated town of Sabiid in the southern region.
The AU mission said the strategic town of Sabiid, which located about 40 km south of Mogadishu, is still controlled by the allied forces.
“Kindly disregard reports circulating that the terrorists have seized the recently liberated town of Sabiid. Sabiid is currently under the full control of Somali government forces with support from AMISOM,” said the AU mission in a statement.
AMISOM said the joint forces continue to work in coordination for peace across the Horn of Africa nation and dismissed the takeover reports as propaganda by the extremist group.
“Al-Shabab and their supporters are at pain with the loss of Sabiid and their inability to face the firm grip of the town by the Somali government forces. They are now resorting to propaganda and disinformation,” said the AU mission.
AMISOM troops in a joint operation with the Somali National Army (SNA) liberated the strategic bridge town of Sabiid from the control of the insurgents on April 1.
Sabiid town, situated in the Lower Shabelle region of Somalia, is one of the strategic objectives which are earmarked for liberation.
Saturday, April 27, 2019
Uganda redCross does not know this... Never fall prey to this fraud!!!
UGANDA RED CROSS JOB APPLICATION FORM
URGENT MASS RECRUITMENT BY UGANDA RED CROSS SOCIETY IN EVERY DISTRICT. APPLY NOW!!!
RED CROSS is a global humanitarian organization that is dedicated to saving lives through provision of emergency responses, health & human development, sanitation, poverty alleviation and food security.
We are recruiting 50 people in every District based on first come first served basis, to fill up the following job positions.
• Supervisors & Administrators
• Cleaners & Messengers
• Fieldwork Assistants
• Guards
• Drivers
• Motorbike Riders
• Accountants
• First-Aid Facilitators
• Nurses
• Receptionists
• Technicians
• Cooks & Caresses
SALARY IS FROM UGX. 940,000 AND ABOVE
Qualifications
1) Must be 18 years and above
2) Understand and Speak English and One local language.
3) Disciplined and ready to work ANYWHERE in Uganda.
Applications must be received on or before 28th April 2019.
* Required
Application Procedure
Step 1: Complete the application form
Step 2: Enter Red Cross Membership number and Submit application.
NOTE: Those who do not have Red Cross membership card must register with 20,000 UGX to get Instant Membership Registration before proceeding with application. The Money is refundable if you do not qualify for the job applied for and do not wish to remain as a Red Cross member.
NOTE: ONLY APPLICANTS WHO HAVE MEMBERSHIP CARDS OR HAVE PAID MEMBERSHIP REGISTRATION FEE WILL BE CONSIDERED.
Step 3: First interview
Step 4: Attend One Week training
Step 5: Receive an offer
MEMBERSHIP FEE PAYMENT PROCEDURE
Note: We have opted for Mobile Money payment mode to make this application process as simple as possible.
1. Go to your Mobile Money menu,
2. Send Money
3.Enter Our MTN NUMBER; 0774 743 298 (ABUBAKALI NDILUGENDAWA, Chief Recruitment Officer)
4. Enter amount 20,000 UGX
5. Enter your PIN and confirm to send money.
POINTS TO NOTE
1. After payment of the Membership Registration fee, you will receive a transaction ID which you will use to complete the application form below. Your Red Cross Membership number will be given to you at a later date.
APPLY BELOW
Name *
First and last name
Your answer
Age *
Your answer
Email *
Your answer
Phone number *
Your answer
Your District *
Your answer
Which job(s) are you interested in? *
You may name a maximum of three
Your answer
Enter your Red Cross Membership Number or Transaction ID you received after sending Registration Fee. *
Your answer
Apply Today To Join The Red Cross Community Around The World

SUBMIT
Friday, April 26, 2019
What are finger print scanner and how does it work
Malicious actors can harm us in so many ways that we cannot even fathom it. The most common tactic they use is by stealing someone’s identification and using it as their own. For this reason, many IT technicians are working on new technologies to get rid of these kinds of menaces. One of the most talked about technologies is Virtual Private Network (VPN). Many people are using free VPNs to attain security, keep their activities anonymous, and encrypt their traffic. However, there is another method of security that many people are unaware of. Technicians gave creation to the technology called Fingerprint Scanners.
What Is A Fingerprint Scanner?
A fingerprint scanner is a device used to identify a person by scanning their fingerprints. We have several ridges on our fingers. Additionally, every person has a unique pattern. Hence, a fingerprint scanner scans them to identify us.
There are also many types of fingerprint scanners. Some of these are as follows:
Optical reflexive
Capacitive
Mechanical
Thermal
Dynamic output
How Do Fingerprint Scanners Work
The sensor avails a light-penetrating microprocessor that can either be a charge-coupled device or a CCD, or a CMOS image sensor. In doing so, this creates a digital picture. Following this, the processor examines the image mechanically, choosing just the fingerprint, and then uses refined pattern-identical software to turn it into encryption.
This is merely how one type of scanner works. In the other kind, i.e., the capacitive type of scanners, the scanner scans the gaps between our ridges.
So when a person places his or her hand on any object, the ridges are the part that touches the surface. Therefore, these ridges are logged and the gaps distances are measured. In this way, the pattern is recorded. In other words, it means the distance between two ridges that never came in contact with the surface is noted down.
Uses Of Fingerprint Scanners
Fingerprint scanners greatly benefit humanity.
They:
are a secure form of identification.
reduce the work of the human brain.
increase the efficiency of work security.
help log people quickly.
Following are some pieces of equipment in which a fingerprint scanner is being used.
1. Laptops and Computers
Fingerprint Scanners are used prominently and most beneficially in our everyday laptops and computers. Thankfully, we have an option of creating a fingerprint configuration. This way, we can keep our laptops and PC’s secure from external attacks. Additionally, we can prevent someone from getting in without permission.
A fingerprint configuration will keep your information safe if you ever lose your laptop.
2. Smart Phone
Smart Phones hold a lot of our personal information. We keep friends/relatives numbers, personal photographs, and sometimes even our notes and private documents. Additionally, in the worst cases, we have banking apps with our credit card information or even social security numbers stored. Therefore, we can use fingerprint arrangement in our phones to keep such information safe and protected.
If your phone is ever stolen, a lock and a fingerprint confirmation will help prevent your information from being leaked or abused.
3. Online Banking
Just like phones and laptops, we also need fingerprint scanners in online banking. Malicious actors often target bank account details like code pins or account numbers. Therefore, using fingerprint scanners ensure that only you can access your bank information.
4. Automatic doors
Today, industrialization has increased so much that office and home security is moving towards automatic doors. However, these doors open only with the correct fingerprint scan. We call this a biometric lock. A person can add their fingerprints to it and then the door will open only when it scans those fingerprints.
Privacy And Security
Of course, we cannot say that fingerprint scanners are 100% reliable. There are ways to hack them. Hackers always find a way to invade into your personal and professional life. Here are some shortcomings regarding fingerprint scanners:
Hackers can use a 3D system of mildew that is created from a preserved fingerprint.
Mischievous and evil hackers can forge your fingerprint with the assistance of tools which are as plain as a luminous or transparent film and a circuit scribe.
Scanners can malfunction and prevent the user from full access if their skin is wet or if too much dust gathers on the devices.
Thus, you see fingerprint scanners does not guarantee privacy. Therefore cyber-crime departments should work more on the security of fingerprint scanners. However, these shortcomings in this relatively new technology does not negate the fact that fingerprint scanners are and will continue to be very helpful and eventually essential.
Tags: Banking,
What Is A Fingerprint Scanner?
A fingerprint scanner is a device used to identify a person by scanning their fingerprints. We have several ridges on our fingers. Additionally, every person has a unique pattern. Hence, a fingerprint scanner scans them to identify us.
There are also many types of fingerprint scanners. Some of these are as follows:
Optical reflexive
Capacitive
Mechanical
Thermal
Dynamic output
How Do Fingerprint Scanners Work
The sensor avails a light-penetrating microprocessor that can either be a charge-coupled device or a CCD, or a CMOS image sensor. In doing so, this creates a digital picture. Following this, the processor examines the image mechanically, choosing just the fingerprint, and then uses refined pattern-identical software to turn it into encryption.
This is merely how one type of scanner works. In the other kind, i.e., the capacitive type of scanners, the scanner scans the gaps between our ridges.
So when a person places his or her hand on any object, the ridges are the part that touches the surface. Therefore, these ridges are logged and the gaps distances are measured. In this way, the pattern is recorded. In other words, it means the distance between two ridges that never came in contact with the surface is noted down.
Uses Of Fingerprint Scanners
Fingerprint scanners greatly benefit humanity.
They:
are a secure form of identification.
reduce the work of the human brain.
increase the efficiency of work security.
help log people quickly.
Following are some pieces of equipment in which a fingerprint scanner is being used.
1. Laptops and Computers
Fingerprint Scanners are used prominently and most beneficially in our everyday laptops and computers. Thankfully, we have an option of creating a fingerprint configuration. This way, we can keep our laptops and PC’s secure from external attacks. Additionally, we can prevent someone from getting in without permission.
A fingerprint configuration will keep your information safe if you ever lose your laptop.
2. Smart Phone
Smart Phones hold a lot of our personal information. We keep friends/relatives numbers, personal photographs, and sometimes even our notes and private documents. Additionally, in the worst cases, we have banking apps with our credit card information or even social security numbers stored. Therefore, we can use fingerprint arrangement in our phones to keep such information safe and protected.
If your phone is ever stolen, a lock and a fingerprint confirmation will help prevent your information from being leaked or abused.
3. Online Banking
Just like phones and laptops, we also need fingerprint scanners in online banking. Malicious actors often target bank account details like code pins or account numbers. Therefore, using fingerprint scanners ensure that only you can access your bank information.
4. Automatic doors
Today, industrialization has increased so much that office and home security is moving towards automatic doors. However, these doors open only with the correct fingerprint scan. We call this a biometric lock. A person can add their fingerprints to it and then the door will open only when it scans those fingerprints.
Privacy And Security
Of course, we cannot say that fingerprint scanners are 100% reliable. There are ways to hack them. Hackers always find a way to invade into your personal and professional life. Here are some shortcomings regarding fingerprint scanners:
Hackers can use a 3D system of mildew that is created from a preserved fingerprint.
Mischievous and evil hackers can forge your fingerprint with the assistance of tools which are as plain as a luminous or transparent film and a circuit scribe.
Scanners can malfunction and prevent the user from full access if their skin is wet or if too much dust gathers on the devices.
Thus, you see fingerprint scanners does not guarantee privacy. Therefore cyber-crime departments should work more on the security of fingerprint scanners. However, these shortcomings in this relatively new technology does not negate the fact that fingerprint scanners are and will continue to be very helpful and eventually essential.
Tags: Banking,
When I wrote about this in early March this year,many of you thought I was joking!!! It's kabale and next is another district... DISOs,GISOs,..... stay warned!!!
Police in Kabale district have arrested Samson Twasiima, the Butanda Sub County National Identification Registration Authority (NIRA) Officer on allegation of bribery and extortion.
The arrest was ordered by Kabale Deputy Resident District Commissioner Gad Rugaju.
Twasiima was arrested on Thursday during a meeting between Mr Rugaju and residents of Butanda, held at Butanda Sub County headquarters.
Rugaju says he called the meeting after several residents reported to his office complaining against the NIRA boss and his colleagues for extorting money from locals who are trying to register for national IDs.
Some of the residents like Winston Tumuheimbise, Elcana Byamukanga and Jonathan Niwamanya told the RDC that the suspect forced them to pay up to Shs 100,000 to accept their applications for the IDs.
Twasiima is also said to have been charging Shs 8000 and 20000 for birth and death certificates respectively from the locals.
In response, Norman Nsenga the Kabale and Rukiga districts NIRA Officer described the situation as unfortunate and apologized for the mess.
He clarified that the registration process for the National IDs is free and all the money supposed to be paid, 5000 for a birth certificate and 50000 for National ID replacement must be paid in the bank.
On his part, Twasiima admitted to have extorted the money from the residents but could not account for it. This forced Rugaju to order for his arrest by police.
The arrest was ordered by Kabale Deputy Resident District Commissioner Gad Rugaju.
Twasiima was arrested on Thursday during a meeting between Mr Rugaju and residents of Butanda, held at Butanda Sub County headquarters.
Rugaju says he called the meeting after several residents reported to his office complaining against the NIRA boss and his colleagues for extorting money from locals who are trying to register for national IDs.
Some of the residents like Winston Tumuheimbise, Elcana Byamukanga and Jonathan Niwamanya told the RDC that the suspect forced them to pay up to Shs 100,000 to accept their applications for the IDs.
Twasiima is also said to have been charging Shs 8000 and 20000 for birth and death certificates respectively from the locals.
In response, Norman Nsenga the Kabale and Rukiga districts NIRA Officer described the situation as unfortunate and apologized for the mess.
He clarified that the registration process for the National IDs is free and all the money supposed to be paid, 5000 for a birth certificate and 50000 for National ID replacement must be paid in the bank.
On his part, Twasiima admitted to have extorted the money from the residents but could not account for it. This forced Rugaju to order for his arrest by police.
Mighty UPDF to get new weapons
A colossal sum of money has been set aside for the purchase of an unnamed item by the Uganda Peoples Defense Forces.
The classified asset is billed at Shs 1.9Trillion, about 6% of the 2019/2020 national budget of 34.3tn.
The Shs 1.94Trillions, is separate from the customary classified expenditure of Shs 225bn also planned for in the same financial year.
The new development is contained in the Ministerial Policy Statement (2019/2020 budget) of Defense and Veteran Affairs ministry.
The annual classified expenditure for the last four financial years since 2015/2016 has been maintained at around Shs 600bn. The 2018/2019 classified expenditure was Shs 640bn.
The planned 2019/2020 total classified expenditure will be Shs 2.2bn, higher than the whole 2018/2019 defense budget of Shs 1.97tn. The 2019/2020 total defense budget stands at Shs 3.4tn, an increment of 58 percent.
The top UPDF generals, Ministers of Defense and Veteran Affairs and Permanent Secretary Rosette Byengoma did not divulge to Members of Parliament any detail about the classified asset during meetings by the Committee on Defense and Internal Affairs sitting at Parliament.
It shall be remembered however, that in mid-2014, the Defense Ministry entered negotiations with a Russian bank through the Russian state owned arms export company, Rosboronexport to acquire a USD$ 170m loan to support the acquisition of some classified equipment.
In 2012 Uganda bought 6 fighter jets from the same Russian state arms export company at Shs 654bn. The government had taken a total of Shs 1.7tn from Bank of Uganda to also buy other military assets from Eastern European countries.
The current Shs 1.94tn (USD$ 524m) can buy 14 multirole Sukhoi Su-30 Russian fighter jets, which are among the most popular in Africa, at the current USD$ 37.5m each. Uganda already has Sukhoi fighter jets in her air force fleet.
The same amount can also buy 112 advanced T-90 third generation Russian made battle tanks. Uganda already own 44 T-90 tanks also known as Vildamirs and the Africa’s biggest defense spender, Algeria (USD$ 10bn) has 572 similar fighter tanks.
Uganda’s Defense spending has also immensely increased from USD$ 500m to USD$ 921m. The defense budget is however projected to reduce to Shs 2.4tn or USD$ 640m in the next financial year of 2020/2021.
When contacted on phone the Ministry of Defense and UPDF Spokesman, Brig. Richard Kaaremire confirmed and defended the budget.
“We need that amount (Shs 1.9tn) to deliver on our mandate as the UPDF,” Karemire briefly said.
The UPDF has four main mandates: to defend and protect the sovereignty and territorial integrity of Uganda, cooperate with civilian authorities in emergency situations and natural disasters, foster harmony and understanding between defense forces and civilians and engage in productive activities for national development.
The Shs 1.9tn for a single classified vote is 48 times bigger than the total 2019/2020 budget of Ministry of ICT and National Guidance’s Shs 40bn.
Subscribe to:
Comments (Atom)
-
A new way for cybercriminals to create fake social media profiles and carry identity scams using Artificial Intelligence powered tool? A ...
-
The Democratic Republic of Congo (DRC) has long been a battleground for complex conflicts, driven by historical betrayals, foreign interfe...
-
- When writing an Android exploit, breaking out of the application sandbox is often a key step. There are a wide range of remote attacks th...












