Hackers used fake ProtonVPN installers to infect users with nasty Azorult malware.
One of the easiest ways to lure users to install malware on their computers is to imitate legitimate websites. This is exactly what certain attackers have done as recently investigated by researchers at Kaspersky by targeting ProtonVPN.
For the unfamiliar, ProtonVPN is a Swiss-based product by the very same company that operates the very famous ProtonMail. Currently, ProtonVPN has more than 2 million users around the world and that makes it a lucrative target for cybercriminals.
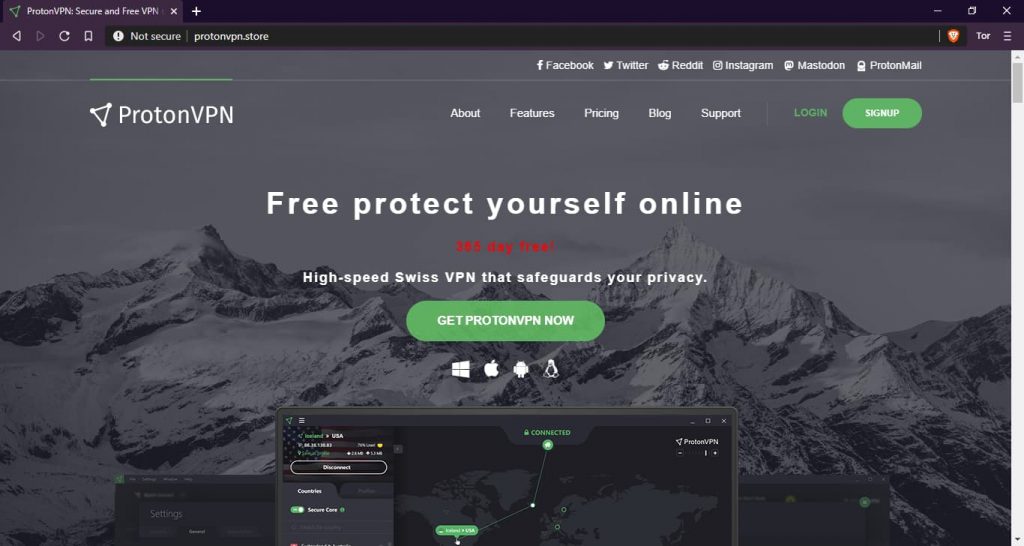
According to Kaspersky, hackers have cloned the design of ProtonVPN’s official website (protonvpn[.]com) to drop AZORult malware through its installer file.
Snapshot of the fake ProtonVPN website:
For your information, Azorult is a RAT (remote access Trojan) that can infect any computer successfully. Azorult was previously found targeting thousands of Magneto sites and spreading PayPal themed banking malware. The same malware was caught last month spreading itself using Drake’s “kiki do you love me” song.
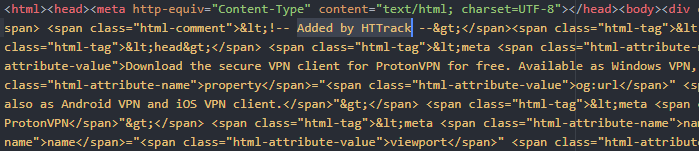
According to Kaspersky’s blog post, to clone the website successfully, hackers made use of a program named HTTrack which made the fake website look similar in its design to the real one.
Therefore, if a user did not know of the original site’s exact domain, they would naturally believe that the site they are visiting is indeed legitimate and hence proceed to download the ProtonVPN installer.
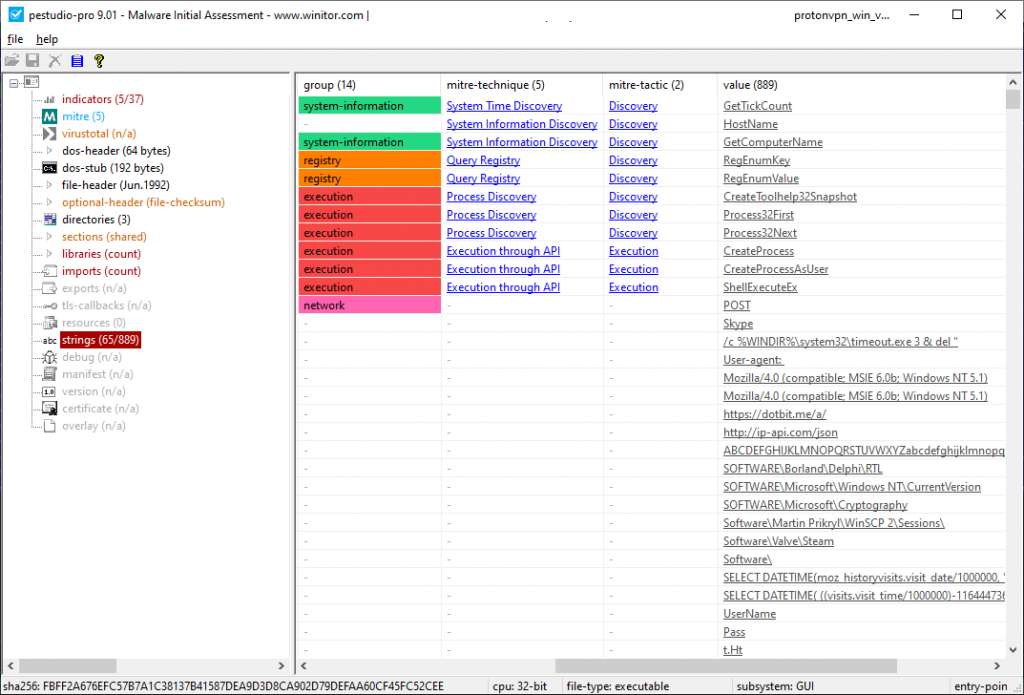
However, instead, they would get AZORult malware in the form of a file named ProtonVPN_win_v1.10.0[.]exe which then can collect highly sensitive information such as one’s passwords, financial information, browsing history, cookies & much more once installed.
The data collected is then relayed to the attackers through their C2 server, also located on their fake website at accounts[.]protonvpn[.]store.
To take things a step further, the AZORult can also steal your cryptocurrencies from any wallets that are locally installed on your computers such as Electrum along with “credentials for WinSCP, Pidgin messenger, and others.”
To add to this, the fake domain was registered in November 2019 through a Russian registrar service. Since then, the attackers have also started targeting users through malicious advertising campaigns, more specifically “affiliation banners networks.”
To conclude, there have been several similar incidents in the past and we can expect them to keep occurring. An example was when we saw fake sites claiming to be official Fortnite distributors spring up prompting users to download malware in actuality. Last year, hackers used similar tactics by cloning the NordVPN website to drop banking trojan.



No comments:
Post a Comment