A UN investigative report has accused the billion-dollar Israeli firm NSO Group of providing spyware to hack Amazon’s president Jeffery Bezos’s iPhone, and the hacker is none other than the Saudi Crown Prince Mohammed bin Salman.
For tho who don’t know, NSO Group is a secretive (not so much now) spyware firm known for making its client capable of conducting offensive-cyber activities. The group was once in the news after one of its employees allegedly stole the company’s secrets with the intention to sell it on the dark web.
The UN report, published Wednesday, claims that Saudi crown prince used malicious spyware developed by the NSO Group to hack Bezos’s phone and stole sensitive private data including his nude selfies.
According to the UN high commissioner for human rights, Bezos’s iPhone was hacked using NSO Group’s spyware Pegasus. The report states that the Pegasus-3 spyware was acquired by the Saudi Royal Guard in November.
It is worth noting that in 2016, NSO Group also made headlines for developing Pegasus, a spyware which in 2016 targeted iPhone devices making them vulnerable to government-sponsored attacks.
In a report published by Citizen Labs and Lookout Security, Pegasus spyware was caught targeting dissidents and activists including Ahmed Mansoor, a renowned human rights activist in UAE.
Reportedly, there was a brief exchange of messages between the Saudi crown prince and Bezos’s back in spring 2018 via WhatsApp. On May 1, 2018, Saudi Crown Prince Mohammed bin Salman sent Bezos’s a video file, which was likely infected with spyware. After the malicious code was executed, a huge amount of data was transferred from Bezos’s phone.
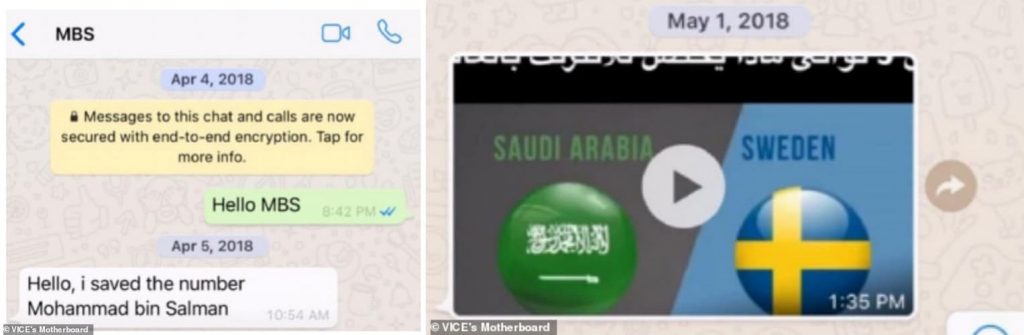
WhatsApp conversation between MBS and Bezos (left) – Video message accused of carrying malware that hacked Bezos’s iPhone (Image credit: Motherboard/Vice)
The NSO Group has previously been accused of providing spyware to countries including Saudi Arabia, Mexico, Panama, and the Middle East for conducting cyberattacks against their adversaries. However, the company denied any involvement.
Nevertheless, this time around too, NSO Group has rejected the report’s claims and is apparently “shocked and appalled” by the news.
“We can say unequivocally that our technology was not used in this instance,” stated the NSO Group.
The timeline of Bezos’s phone hack is integral, claims the UN report, because around the same time the phones of two very close associates of late journalist Jamal Khashoggi were hacked using the same spyware. The UN has asked the US and other authorities to take notice and investigate the matter on an immediate basis.