The new report claims that Iranian hackers have been targeting Israel and other countries with this campaign.
According to the findings of the UK-based cybersecurity firm ClearSky, an Iranian APT group has been running a widespread hacking campaign to compromise VPN servers and install backdoors or bugs to access networks of different organizations across the globe.
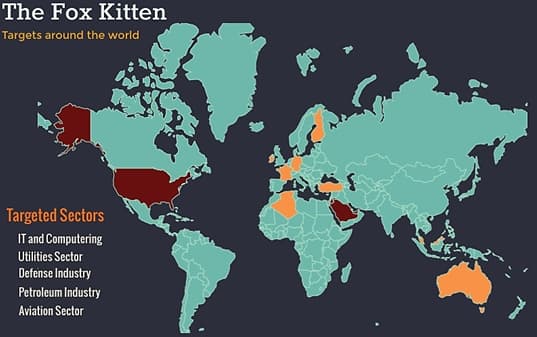
Dubbed Fox Kitten; the campaign was launched three years back (2017) to target “dozens of companies and organizations in Israel around the world,” the company stated in its official statement.
The attackers successfully infiltrated networks of many organizations across diverse sectors from IT, oil and gas, telecom, security, and government. The organizations have footprints throughout the world, which makes this campaign a global scam.
The alarming fact is that during this operation, Iranian hackers not only gained access to the networks of so many organizations around the world but made sure that they were able to hijack the device for as long as they wanted to.
Using the campaign, hackers could develop and maintain access routes to their target companies and obtain sensitive data.
“Hackers maintained a long-lasting foothold at the targeted organizations and breach additional companies through supply-chain attacks,” researchers said in their blog post.
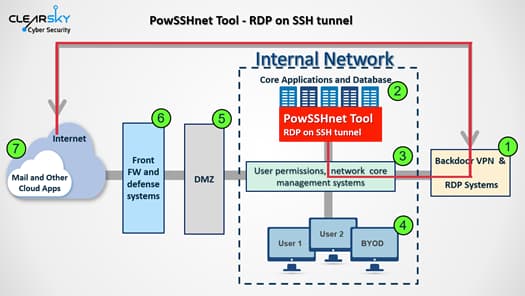
To pull off the attack, hackers used different tools, a majority of which were open-source software while some were self-enveloped. As per previous research, the most successful attack vector that Iranian hackers have used so far is the exploitation of systems vulnerabilities encouraged by unpatched RDP and VPN services.
Once they are able to access the organizational networks, they tend to create more access points to reach the core corporate network. This is why closing one access point doesn’t affect their capability of monitoring company networks.
In fact, ClearSky claims that Iranian APT groups can exploit VPN flaws in a few hours, as soon as the bug is disclosed. ZDNet reports that Fortinet, Pulse Secure, Citrix VPNs, and Palo Alto Networks are some of the targets of Iranian hacker groups.