EventBot malware has been active since March 2020.
Being a major mobile platform, Android is frequently targeted by hackers because of the lucrative benefits associated with it. That’s one major reason Android users normally find themselves coming across new types of malware built for the platform almost everyday.
Such is the case of a recent report by the Cybereason Nocturnus team who has discovered a new type of android Malware dubbed EventBot first seeing it in March 2020. To continuously accomplish its purpose, the attackers behind this malware have been releasing new versions with improvements & increased functionality over time. Currently, 4 of these were found named Version 0.0.0.1, 0.0.0.2, and 0.3.0.1 and 0.4.0.1.
The malware is believed to be a banking trojan and infostealer that exfiltrates important financial data from over 200 banking and cryptocurrency apps. This data is comprised of personal data, passwords, keystrokes, and banking information among others allowing EventBot to hijack transactions.
The targeted apps include the likes of PayPal, Coinbase, Barclays, Santander UK, and HSBC UK, among others, pointing to the fact that the majority of them are based in the United States & Europe in countries such as Italy, the UK, Spain, Switzerland, France, and Germany.
EventBot uses different techniques to gain unauthorized access. Firstly for it to get installed on the victim’s device, it poses as a legitimate application on different third-party app stores. Unsuspecting users download these leading to the malware gaining a hold on their device.
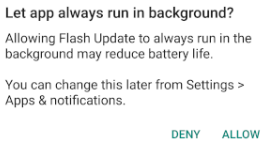
Once installed, it asks for permissions that it does not need including but not limited to accessing accessibility features, reading from external storage, letting the app run & use data in the background, allowing it to install packages & open network sockets, and open & read text messages. The lattermost permission also allows it to bypass two-factor authentication (2FA).
All of these then allow EventBot to function unhindered as a keylogger collecting data from any open windows and other applications. To send the collected data back to the attackers, it also downloads C2 server URLs with the data sent is encrypted using Base64, RC4, and Curve25519 depending on the respective version currently operating.
Concluding, coming to the question of attribution, Cybereason said in its blog post that they could not find any sources connected to it on “underground communities”. One reason may be that EventBot is “still undergoing development and has not been officially marketed or released yet.”
For Android users who may be concerned, as evident, the easiest way to avoid being infected is to not install apps through third-party stores and stick to Google's playstore. Moreover, EventBot should not be underestimated because as in the words of the researchers themselves,
This brand new malware has real potential to become the next big mobile malware, as it is under constant iterative improvements, abuses a critical operating system feature, and targets financial applications.





No comments:
Post a Comment