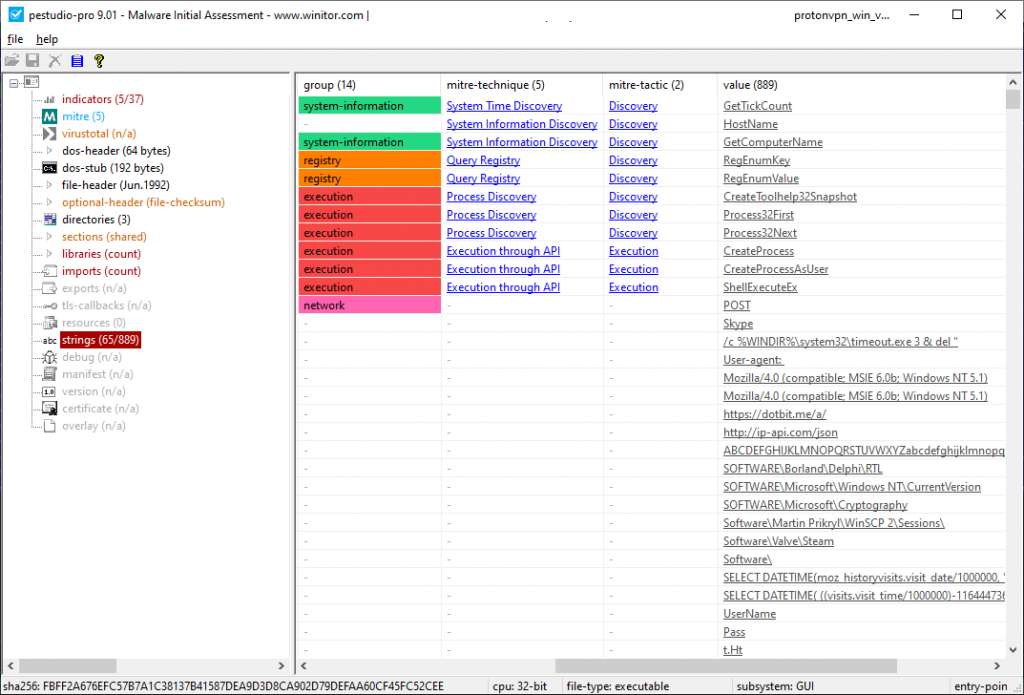
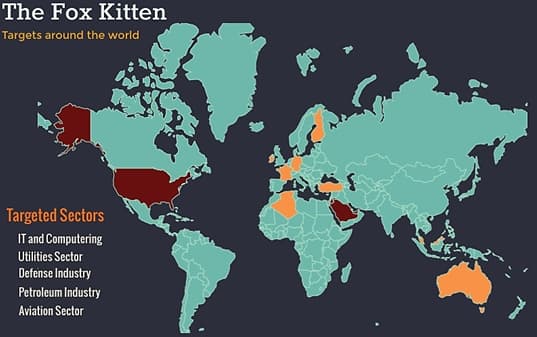
The US Army began the development of its ‘Strategic Long-Range Cannon (SLRC) in late 2019, with the weapon expected to have a range of up to 1,850 km. The military expects a demonstration prototype to be created by 2023.
The Twitter account of the US Army’s Combat Capabilities Development Command Research Laboratory has shown what appear to be the first prototype images of the SLRC supergun, with a high-res photo of engineers speaking to US and British officers showing an image of the SLRC in the background, with its overall design and key capabilities clearly visible.
The @USArmy hosted a US-UK Modernization Demonstration Event Feb. 20 at @USAGAPG to identify capability collaboration to the British Army. Officials from @ArmyFutures
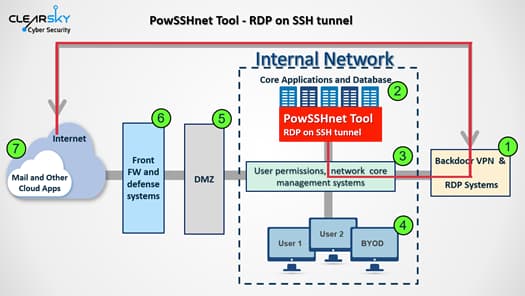
@USArmyCCDC , the centers and the lab, briefed interoperability to minimize risks of #modernization divergence. pic.twitter.com/Hw3V7xJFgA
— U.S. Army CCDC Army Research Laboratory (@ArmyResearchLab)
February 21, 2020
An image of the unit shows that it is transported by a conventional 14 wheel military hauler, possibly an Oshkosh M1070 of the kind used to carry tanks, with the gun attached to the transport via two separate pieces.
According to the poster printed out by Army Futures Command, the system is designed to penetrate and destroy “enemy A2/AD [anti-access/area denial] defences to create windows of opportunity for exploitation.” The system is expected to have a range “beyond 1,000 miles,” a crew of 8 personnel per platform, and 4 platforms per battery. The system is designed to be transportable by sea and air.
The photos of the SLRC were taken at a joint US-UK ‘Modernization Demonstration Event’ at the Aberdeen Proving Ground northeast of Baltimore, Maryland on February 20. US officials were said to have briefed their British comrades on interoperability “to minimize risks of #modernization divergence.”
The SLRC programme is designed in part to serve as a cost-effective alternative to more expensive munitions, with rounds for the system expected to cost “only $400,000 or $500,000” apiece compared to the multi-million dollar apiece missiles. Last year, Col. John Rafferty, director of the Army’s Long-Range Precision Fires Cross Functional Team, said that if the SLRC was adopted, it would complement the military’s hypersonic missiles in penetrating enemy territory at a “more affordable” price per shot.
The Twitter account of the US Army’s Combat Capabilities Development Command Research Laboratory has shown what appear to be the first prototype images of the SLRC supergun, with a high-res photo of engineers speaking to US and British officers showing an image of the SLRC in the background, with its overall design and key capabilities clearly visible.
The @USArmy hosted a US-UK Modernization Demonstration Event Feb. 20 at @USAGAPG to identify capability collaboration to the British Army. Officials from @ArmyFutures
@USArmyCCDC , the centers and the lab, briefed interoperability to minimize risks of #modernization divergence. pic.twitter.com/Hw3V7xJFgA
— U.S. Army CCDC Army Research Laboratory (@ArmyResearchLab)
February 21, 2020
An image of the unit shows that it is transported by a conventional 14 wheel military hauler, possibly an Oshkosh M1070 of the kind used to carry tanks, with the gun attached to the transport via two separate pieces.
According to the poster printed out by Army Futures Command, the system is designed to penetrate and destroy “enemy A2/AD [anti-access/area denial] defences to create windows of opportunity for exploitation.” The system is expected to have a range “beyond 1,000 miles,” a crew of 8 personnel per platform, and 4 platforms per battery. The system is designed to be transportable by sea and air.
The photos of the SLRC were taken at a joint US-UK ‘Modernization Demonstration Event’ at the Aberdeen Proving Ground northeast of Baltimore, Maryland on February 20. US officials were said to have briefed their British comrades on interoperability “to minimize risks of #modernization divergence.”
The SLRC programme is designed in part to serve as a cost-effective alternative to more expensive munitions, with rounds for the system expected to cost “only $400,000 or $500,000” apiece compared to the multi-million dollar apiece missiles. Last year, Col. John Rafferty, director of the Army’s Long-Range Precision Fires Cross Functional Team, said that if the SLRC was adopted, it would complement the military’s hypersonic missiles in penetrating enemy territory at a “more affordable” price per shot.